8.2 Information Technology Services (ITS) Based Resources
The IT department offer adequate and up-to-date technology in all the classrooms, laboratories, and library for their use by its faculty, staff and students to ensure that the University meets all the needs and requirements of the program offerings, as well as, meet the university’s programmatic needs which include, but not limited to, learning, teaching, and research. IT based facilities provided are as listed below:
IT Department updates UD equipment and software regularly and resolves as quickly as possible any problems that develop which may hinder the network operation, individual faculty and staff workstations, or computer labs.
- Faculty and staff at UD have the following IT infrastructure and services:
- Dedicated desktop machine with flat screen monitor
- Laptops are provided upon request from the IT Services
- Logon accounts are created for each staff/faculty member as per the UD policies
- Each college has a centralized laser-printer server located within the colleges and few faculty members have individual printers.
- University resources Application (UDSIS, UDLIBRARY, UDMAIL, UDMOODLE and CAMS) can be accessed from remote locations through the UD website.
- Internet access
- UD licensed software is installed on all the faculty/staff computers.
- IT services provides laptops that are essentially used for presentation purposes to staff and faculty.
- UD students have the following IT infrastructure and services:
- Each student has his/her own student logon account as well as email address.
- UD campus has 10 labs which are available for the students from Sunday to Thursday from 8:30AM – 10:00PM and on Saturday from 10:00AM – 10:00PM.
- Labs are also available during the weekends with an approval from the IT Services team.
- Library computers can be used at any time during the library’s working hours.
- Internet access is available 24/7.
- Each student has a user roaming profile which helps the student in accessing his or her folder from any workstations in UD
- Each lab is equipped with a laser printer.
- UD standard licensed software is installed in all the labs.
- UD classrooms have the following IT infrastructure and services:
- Each classroom has PC, LCD Monitor and Speaker
- Each lab is equipped with one or more of finger print machine for student’s attendance
- UD standard licensed software is installed in all classrooms
- Workstations/Servers:
Following Table shows a List of Workstations/Servers
| SN |
Workstations/Servers |
| 1. |
Domain Controller |
10. |
Windows Server Update Service |
| 2. |
Students Information System |
11. |
Library Server Resource |
| 3. |
Kaspersky Antivirus |
12. |
Fingers Print Server Controller |
| 4. |
Files share with Symantec Backup Server |
13. |
Printers Servers Controller |
| 5. |
Helpdesk Spice work System |
14. |
Password Manager AD Self |
| 6. |
Accenting System Great Plains |
15. |
NAS Storage System |
| 7. |
Web Proxy |
16. |
Backup Tape System |
| 8. |
Moodle Learning Management System |
17. |
UPS System |
| 9. |
Telephone Log System |
|
|
- Network Infrastructure
The IT Department ensures that a reliable network is in place enabling all members of the institution’s community to use IT and to access information/resources. The University is equipped with fiber optical cables and is covered with wireless connection which allows students to access internet from the 2nd floor and library. In the library it has 26 wired and in the 2nd floor and 4th floor students can use wireless connection. The 6th floor is connected by core switch to each floor and then through each floor it is connected by a cable network.
- IT Support Services:
The IT support services include delivering technical services, solutions, practices and guidelines for the UD community. The IT service monitors daily operations of UD network and all PCs and labs used by faculty, staff and students. The IT Services department constantly plan ways to improve the technology available, increase efficiency and reduce downtime. The procedures followed for handling helpdesk requests, website maintenance, and creating e-mail accounts are described below:
- Providing user support through Helpdesk
- Maintaining and Updating Website
- Creating E-Mail Accounts
- Developing IT Solutions
IT Department is well equipped to provide IT Solutions to its users who intend to customize and develop solutions using the existing and internally developed/customized IT solutions as summarized in the Table below. These solutions employ the usage of appropriate “database” structures that support the design of customized user-friendly interfaces.
A list of databases employed in offering IT Solutions – A summary listing
| SN |
System |
Database |
| 1. |
Student Information System (SIS): Admission; Registration; Class Schedule; Classroom Booking; Student Advising; Online Registration System |
Oracle DB 10g |
| 2. |
UD Survey System |
MYSQL DB 5 |
| 3. |
Paper Cut System: paper quota for student |
|
| 4. |
Moodle System: learning management system |
SQL 2008 |
| 5. |
SugarCRM: customer relationship management for marketing and recruiting |
SQL |
| 6. |
Spicework: helpdesk system |
SQL 2008 |
7.
|
Fingerprint System |
SQL 2005 |
| 8. |
Financial Management (Great Plains) |
SQL 2005 |
- Hardware Maintenance & Upgrades
The IT Services department ensures that appropriate measures are taken to maintain and upgrade all existing hardware in line with current technologies. The following describes UD strategy:
- A life cycle of five years is expected for all PC depending on their usage; therefore, in general, third of the existing PCs within the college are expected to be upgraded or replaced depending on request.
- Servers, LAN, and Internet related equipment are examined yearly and upgrades’ needs are determined.
- Peripherals such as printers, scanners, projectors, etc. may have a life cycle of more than three years depending on their usage. Such equipment’s are examined yearly and their replacement is determined.
- Shared network drives
In order to safeguard the data; all the files have to be stored only in the shared folders to help in the back up procedure and prevent from any loss of data, as mentioned below:
- Student Folders (S: Drive): Files stored in this drive will be accessible only for students and faculty to that particular department thus providing the flexibility for the users to share the information.
- General Folders (G: Drive): Each department is assigned a folder that is accessible to them only. This helps in centralized the data in one place.
- Public Folders (P: Drive): accessible by all faculty and staff; share information about the different events, activities and other work related documentation.
- Home Folders (H: Drive): Each faculty and staff are assigned a folder to store their files so that it will be easier to access them if shift from one place to another.
- Back-up Policy
IT Department has a Detailed Schedule of Back-up Policy. The Backup plan is to perform backups on a daily, weekly, monthly and yearly basis with combination of full and differential backups based on File types as summarized in the table below:
Table showing a summary of the IT Dept. Back-up Schedule
| File Type |
Daily |
Weekly |
Monthly |
Yearly |
| Shared Folders (Department, Public & Home) |
✔ |
✔ |
✔ |
✔ |
| SQL |
✔ |
✔
|
✔
|
✔ |
| System State |
|
|
✔ |
|
| Oracle DB |
✔ |
✔ |
✔ |
✔ |
| MOODLE DB & data |
✔ |
✔ |
✔ |
✔ |
| Applications |
✔ |
✔ |
✔ |
✔ |
Table showing IT Scheduled Timings for Backups
| Backup Type |
Start Time |
| Daily – Differential |
23:00 |
| Weekly – Full |
10:00 |
| Monthly – Full |
23:00 |
| Yearly – Full |
23:00 |
Tape Rotation is scheduled as below.
| Table: Daily Differential Backup |
Table: Weekly Full Backup |
| Week |
Day |
Overwrite protection |
| 1 |
Sun |
Mon |
Tue |
Wed |
Thu |
26 days |
| Wk2 |
Sun |
Mon |
Tue |
Wed |
Thu |
26 days |
| Wk3 |
Sun |
Mon |
Tue |
Wed |
Thu |
26 days |
| Wk4 |
Sun |
Mon |
Tue |
Wed |
Thu |
26 days |
| Wk5 |
Sun |
Mon |
Tue |
Wed |
Thu |
26 days |
|
| Week |
Day |
Overwrite Protection |
| Wk1 |
Friday |
26 days |
| Wk2 |
Friday |
26 days |
| Wk3 |
Friday |
26 days |
| Wk4 |
Friday |
26 days |
| Wk5 |
Friday |
26 days |
|
| Table: Monthly Full Backup |
| Month |
Overwrite Protection |
| Jan |
52 days |
| Feb |
52 days |
| Mar |
Quarter 1 - 360 days |
| Apr |
52 days |
| May |
52 days |
| Jun |
Quarter 2 - 360 days |
| Jul |
52 days |
| Aug |
52 days |
| Sep |
Quarter 2 - 360 days |
| Oct |
52 days |
| Nov |
52 days
|
| Dec |
Year End Backup - Preserved |
Note: All the tapes are stored in a fire-resistant safe at Dubai Chamber building.
- Assessing Needs
A yearly assessment of IT needs is conducted by the IT Committee which meets during the last week of May to assess UD’s needs (purchases, upgrades, replacement and maintenance) in terms of new IT hardware and software. The IT Committee requests from the various UD functional units to submit their IT needs.
Table: Server Inventory- HP Servers
HP Servers
|
| # |
Server Model |
RAM (GB) |
HDD (GB) |
CPU |
| 1. |
HP ProLiant DL380 Gen5 |
4096 |
146 |
Intel(R) Xeon(R) CPU E5420 @ 2.50GHz |
| 2. |
HP ProLiant DL380 Gen5 |
6144 |
146 |
Intel(R) Xeon(R) CPU E5335 @ 2.00GHz |
| 3. |
HP ProLiant DL380 Gen6 |
8192 |
730 |
Intel(R) Xeon(R) CPU E5530 @ 2.40GHz |
| 4. |
HP ProLiant DL380p Gen8 |
32768 |
600 |
Intel(R) Xeon(R) CPU E5-2620 0 @ 2.00GHz |
| 5. |
HP ProLiant DL380p Gen8 |
32768 |
600 |
Intel(R) Xeon(R) CPU E5-2620 0 @ 2.00GHz |
| 6. |
HP ProLiant DL380p Gen8 |
32768 |
600 |
Intel(R) Xeon(R) CPU E5-2620 0 @ 2.00GHz |
| 7. |
HP ProLiant DL380 Gen9 |
32768 |
1500 |
Intel(R) Xeon(R) CPU E5-2620 v3 @ 2.40GHz |
| 8. |
HPE StoreEasy 1650 E Strg |
8192 |
8000 |
Intel(R) Xeon(R) CPU E5-2609 v3 @ 1.90GHz |
|
|
|
|
|
| Table showing Server Inventory- IBM Flex Server |
| IBM Flex Server (Private Cloud Virtual Infrastructure) |
| # |
Server/Device Model |
RAM (GB) |
HDD (GB) |
CPU |
| 1. |
IBM Flex Enterprise Chasis |
|
|
|
| 2. |
IBM Flex Manager |
|
1000 |
|
| 3. |
IBM Flex System x240 Compute Node |
131072 |
300 |
Intel(R) Xeon(R) CPU E5-2660 0 @ 2.20GHz |
| 4. |
IBM Flex System x240 Compute Node |
131072 |
300 |
Intel(R) Xeon(R) CPU E5-2660 0 @ 2.20GHz |
| 5. |
IBM Flex System x240 Compute Node |
131072 |
300 |
Intel(R) Xeon(R) CPU E5-2660 0 @ 2.20GHz |
| 6. |
IBM Flex System V7000 Storage Node |
|
7000 |
|
Table showing Applications Inventory
| SN |
Application |
Description |
Usage |
Faculty |
Staff |
Students |
| Teaching |
Research |
| 1. |
Microsoft Office 365 & Pro Plus |
Productivity suit |
✔ |
✔ |
✔ |
✔ |
✔ |
| 2. |
Google Apps |
Productivity suit |
✔ |
✔ |
✔ |
✔ |
✔ |
| 3. |
SPSS |
Data and statistical analysis application |
✔ |
✔ |
✔ |
|
✔ |
| 4. |
Stata |
Data and statistical analysis application |
✔ |
✔ |
✔ |
|
✔ |
| 5. |
SmartPLS |
Structural equation modeling application |
✔ |
✔ |
✔ |
|
✔ |
| 6. |
Adobe DreamWeaver |
Web development application |
✔ |
✔ |
✔ |
|
✔ |
| 7. |
Adobe Acrobat Reader |
PDF reader |
✔ |
✔ |
✔ |
|
✔ |
| 8. |
Adobe Digital Editions |
e-Book reader |
✔ |
✔ |
✔ |
|
✔ |
| 9. |
7Zip |
File compression utility |
✔ |
✔ |
✔ |
✔ |
✔ |
| 10. |
Java with Netbeans |
Programing language and development kit |
✔ |
✔ |
✔ |
|
✔ |
| 11. |
PSPad |
Text editor |
✔ |
✔ |
✔ |
✔ |
✔ |
| 12. |
NotePad ++ |
Text editor |
✔ |
✔ |
✔ |
✔ |
✔ |
| 13. |
PSPP |
Data and statistical analysis application |
✔ |
✔ |
✔ |
|
✔ |
| 14. |
VenSIM |
Simulation application |
✔ |
✔ |
✔ |
|
✔ |
| 15. |
Brackets |
Text editor |
✔ |
✔ |
✔ |
|
✔ |
| 16. |
PDFill |
PDF creator and editing utility |
✔ |
✔ |
✔ |
✔ |
✔ |
| 17. |
MatLab |
Mathematical computing software |
✔ |
✔ |
✔ |
|
✔ |
| 18. |
EViews |
Data and statistical analysis application |
✔ |
✔ |
✔ |
|
✔ |
| 19. |
Adobe Productivity Suit |
Productivity suit |
✔ |
✔ |
✔ |
✔ |
✔ |
| 21. |
Sophos EndPoint Protection |
Security |
✔ |
✔
|
✔ |
✔ |
✔ |
- Office Hours
For all IT related problems and requirements IT helpdesk can be contacted by users on +97145566888 or email helpdesk@ud.ac.ae between 8:30AM to 10:00PM Saturday to Thursday. Besides, helpdesk is available during all scheduled classes for needed support.
The IT department created ‘How-To’ guides and manuals, as well as video tutorials for the various technologies and services that are provided by the department. These resources are available on the University’s website, and internal document repositories for open access. The department also provides training to faculty, staff, and students on these various technologies and services periodically and on request.
The University has various platforms such as Moodle and CAMS, which both have email, chat, and announcement features that enable efficient communication between the University, students, and faculty. Both faculty and students also use these platforms for communication and course materials sharing. The University has also made available to all staff, faculty, and students other communications platforms such as Skype for business and Google Hangouts.
- Moodle (Course Management System)
- CAMS (Student Information System)
UD’s network topology is designed to offer as much reliability as possible. Each core network device (firewall and switches) has a primary and secondary device, which means in the event of a failure there is always a spare to continue functioning. The network itself is divided into multiple subnets that are independent of each other, and do not allow communication between them to mitigate un-authorized access of data and resources.
Below is a summary network topology for the University:
Summary Network Topology for UD
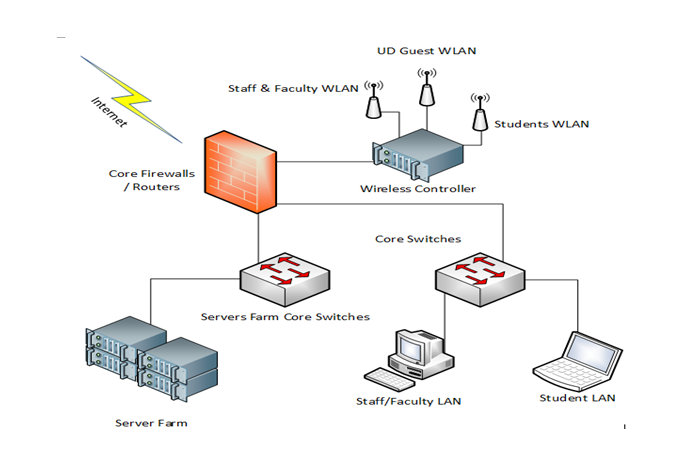
Level of IT network Reliability: Provided below are few excerpts on the network reliability as an example:
- The student computers on the students wired LAN (i.e. library and lab computers) can only connect to the student network and cannot access data and resources on the staff/faculty network, and vice-versa.
- Staff/faculty connected to the staff/faculty wired network can only connect to this network and only access data and resources on this network. They cannot access data and resources on the student networks.
- Users connected to the student WLAN cannot access any wired network, both student and staff/faculty.
- Users connected to the Guest WLAN cannot connect to any network or access any data or resource. These users only have access to the internet.
Table showing the Audit Maintenance of the IT Network
| Category |
Tasks |
| Operational Support |
Perform monitoring, maintenance, backup, log analysis, and recovery testing for servers and applications. Provide troubleshooting, operations, maintenance, administration, application, network, migration, and database support. |
| Software Maintenance and Upgrades |
Provide software development and maintenance services for custom computer system solutions using the full system development life cycle (SDLC). |
| Infrastructure Management Services (IMS) |
Manage the entire applications infrastructure capability for the environments described above. |
| Configuration Management |
Conduct configuration management for the applications infrastructure capability including server, operating system and vendor inventories, patching and upgrade services, and software migration services. |
| Network/Hardware Support |
Provide hardware technical support for servers responsible for monitoring performance of installed applications and servers. Administer vendor changes/patches and conduct performance tuning. |
| Help Desk/IT Support |
Operate help-desks and provide training for applications and network support operations, and receive requests for services. The IT infrastructure help-desk also provides “last tier” support to the separate applications help-desks to resolve network and interconnectivity problems. |
| Resource Management |
Manage the network infrastructure resources, and asset/software resources. |
| Backup and Recovery Management |
Implement and manage backup/archive strategies for systems and servers. Perform backup, storage, and disaster recovery functions. |
| Installation, Configuration, and Tuning |
Provide installation, configuration, and tuning services. DBA’s, network specialists, and Linux and Windows server administrators monitor system performance and coordinate tuning and performance solutions. |
| Electronic Software Licensing Services |
Provide support to manage assets, licenses, maintenance agreements, production migrations, patch management, software/hardware vendor upgrades. |
| System Management |
Track computer systems and services, perform migration and change management services, ensure audit compliance, coordinate releases, and monitor post-deployment performance, changes, and relationships with system sponsors and end users. |
| IT Training |
Conduct training for a full suite of IT applications. |
| IT O&M Planning |
Perform capacity-planning analysis, and make new server recommendations, configuration change recommendations, and financial recommendations for hardware/software acquisitions. |
| Transformation Services |
Support the IT cultural transformation needed to evolve in-house and support transformation services with respect to IT trends. |
| Continual Service Improvement |
Work with system sponsors, government personnel, end users, development and support teams, and other contractors to monitor, support, and continually improve technical and relationship services to partners. |
| IT Infrastructure Optimization |
Analyzed and implemented virtualization techniques to reduce server inventories, heat production, air conditioning requirements, and rack space needs by eliminating the requirement for physical servers unless absolutely necessary. Active participant in a Data Center Consolidation Initiative producing analysis and metrics and submitting reports to the department as coordinated with government personnel. |
Other Maintenance and reliability assurance tasks include:
- Server and storage infrastructure
- Desktop infrastructure
- Network equipment
- Backup and security systems
- Patch management
- Log file review and corrective action
- Security vulnerability testing
- Anti-Virus and Anti-Spam management
- Active directory account review
- Archiving and data file management
- Routine backup verification and test restores
- Threshold trending and management – CPU, RAM, disk, network bandwidth
- Application interoperability and alerts
- Asset management tasks
- Custom maintenance tasks developed to meet unique requirements.
Note that many maintenance tasks are performed in “real-time”. That is, we use our monitoring and IT Management Systems to automatically raise alerts based on pre-defined thresholds or known error conditions, which are then actioned by our network maintenance team as they happen.
As documented in UD Policies & Procedures # LR 7.1, the University currently has a policy of replacing student and faculty computers at a maximum device age of 5 years. Devices are also upgraded at any point within the 5 years whenever there is a requirement for an upgrade due to growing demands. However, some devices are replaced before the 5 years with newer, higher specification devices depending on the requirements at the time
The University currently has anti-virus applications on all computers which have features that mitigate all know security threats at this point in time (such as malware, crypto ware, Trojans, etc.). UD’s ID employs firewalls on the perimeter of our network that secure our network from outside threats. These devices also segregate the internal network into different sub-networks, which allows us to restrict user access to networks that they are authorized to access. For example, students are not able to access staff and faculty subnetworks whether they are connected to the University network using wireless or through the University’s student computers.
Security protocols are also in place to secure the computers and other hardware as well, in order to prevent data loss and protect the integrity and confidentiality of user and administrative data. One such protocols are the blockage of the use of USB drives on student computers.
UD plans also to have an internal network firewall, antivirus controller, and security operations center controller to provide advanced insight into our security infrastructure as well as enhance our internal security.
The University currently has an in-house developed application (FQIS) for managing faculty data such as research, publications, scheduled teaching, etc. The University also employs applications such as Moodle for course management, and CAMS for the management of student information. Moodle provides a platform where faculty can monitor the courses they teach, as well as share course resources, conduct assessments, and communicate with their students. CAMS, on the other hand, are a platform where students can track their whole information. This includes course audits, grades, finances, announcements and communications, course registrations, etc. There also is a course file management system created through the utilization of the folder management feature of the Windows Server to provide secure and private course file storage for all faculty.
The University has also made available applications such as Tableau, to relevant departments, for the mining and analysis of the University data and reporting.